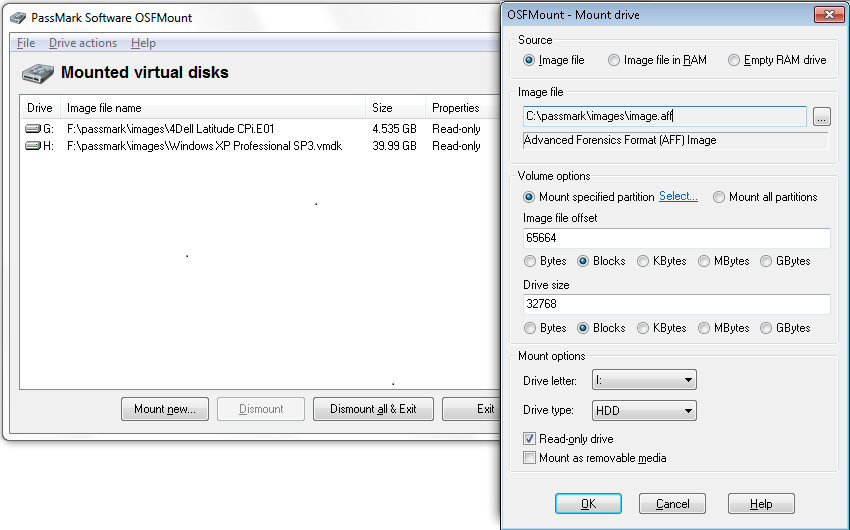
OSFMount is the perfect tool for mounting a dd file in Windows and mapping that to a drive letter. This allows you to run your preferred data recovery tool against a dd file that you have created, using a tool like dd or GNU ddrescue.
Below is an overview of your options with different types of drive images.
| Image Format | Read | Write | Mount as RAM drive | Convert to Image file | Extend | Format |
| Raw Image (.IMG, .DD) | ||||||
| Raw CD Image (.ISO, .BIN) | ||||||
| Split Raw Image (.00n) | ||||||
| Nero Burning ROM Image (.NRG) | ||||||
| System Deployment Image (.SDI) | ||||||
| Advanced Forensics Format Images* (AFF) | ||||||
| Advanced Forensics Format Images w/ meta data* (AFM) | ||||||
| Advanced Forensics Format Directories* (AFD) | ||||||
| VMWare Image (.VMDK) | ||||||
| EnCase EWF (.E01) | ||||||
| SMART EWF (.S01) |